 How to Manage the Risk of Cyber Attacks
How to Manage the Risk of Cyber Attacks
i3 Business Solutions is a first-generation family business owned and run by Mike Ritsema, and his son, Marcus. Founded in 2004, the business is headquartered in Grand Rapids and has offices in Farmington Hills. In honor of Tech Week GR 2023, they have provided Member Insights on Cybersecurity for family Businesses.
i3 Business Solutions becomes or assists the technology department for almost 100 companies and 4,000 end users in the State of Michigan.
Cybersecurity Threat
Despite layers of cybersecurity protection, every month we continue to see compromises to Michigan businesses’ technology. How can this be?
According to the Verizon 2023 Data Breach Investigations Report (DBIR) 50% – that’s half of all cybersecurity incidents are due to social engineering. That means mistakes by the ‘human firewall.’ Furthermore, 74% – that’s ¾ of all breaches involve the human element – again, that’s mistakes by people in our companies. Human error.
The three primary ways that cyber attackers access organizational data are:
- Stolen credentials
- Phishing – whale or spear phishing
- Exploitation of vulnerabilities.
The Microsoft image displayed is an example of mistakes people make on a regular basis.
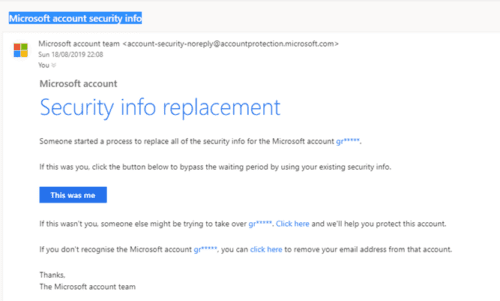
“Oh, I need to login again to confirm my account,” we think.
“Oh, I have a security alert and have to confirm my identity,” we click away as we rush through our day.
Clicking on the fake link and entering my login, password, and 2-Factor authentication hand our credentials to the threat actors. They’re going to work. They’re moving around in my network or Microsoft 365 or Google Business Suite account. They’re in there and will lay in wait for weeks or months – watching, learning, scheming, planning the way they’ll exploit the information.
More and more, cybercriminals are creating near perfect narrowly targeted emails directed at owners, executives, finance, and technology professionals. We call this whale or spear phishing.
Protection
That socially planned targeted attack means that all the firewalls and antivirus in the world can’t stop our employees from making a mistake! We must figure out how to protect our businesses from ACH mistakes, ransomware, and data exfiltration.
In cybersecurity we say it’s not if you’ll be hacked but when you’ll be hacked. Sad but true.
Action:
What are the top 7 things we can do to protect our businesses?
- Test & educate your team using a structured cybersecurity phish testing and training system.
- Implement Multifactor Authentication (MFA – 2-Factor) across ALL cloud or online systems – especially email.
- Implement Multiperson Authentication within your financial controls. That is, any change to ACH checking and routing account numbers or payroll data must be confirmed by a second person and a phone call to a known number to hear a (known) person’s voice.
- Implement Endpoint Detection & Response (EDR) which is the next generation antivirus that not only protects our PCs, Laptops, Macs, and servers – but also detects and automatically responds to threats.
- Review, manage, and deactivate former employee accounts and administrator rights across all relevant systems.
- Buy cybersecurity insurance.
- Confirm that you have a discrete offsite air-gapped backup to your most important information and data. Can you actually restore from those backups?
Responsibility & Risk:
Business owners, partners, executives, and managers focus on 4 business functions:
- Profitability – sustainability
- Productivity – efficiency
- Differentiation – value proposition
- Risk mitigation.
For me, risk mitigation is the highest on that list. We manage many risks in business: financial, physical, employee, and financial are just a few. During the Great Recession 15 years ago and the 2020 Covid-19 pandemic, managing the financial risk of i3 Business Solutions was my highest priority. We manage risk with various controls and review processes to assure consistent operation and growth.
Your IT Manager or technology provider are the stewards of your technology risk. You, the family business owner, partner, shareholder, or executive team own the risk.
Collar your IT Manager or technology provider and ask the above seven questions. Oh, a couple of them go to your Finance Manager or accounting assistant. Copy / paste and email the list to the appropriate individuals.
There are 18 controls and 153 safeguards in the Center for Internet Security’s cybersecurity framework. Get started today by asking the above 7 questions. Consider a wider cybersecurity assessment if you’re more concerned.



Leave a Reply